Our Commitment to Your Data’s Security
At QA Sphere, protecting your data isn’t just a priority—it’s a responsibility we take seriously. The safety and integrity of your information are at the core of everything we do. By implementing robust security protocols and adhering to industry best practices, we ensure your sensitive information is protected against potential threats.
From encrypted data transmission to secure infrastructure, every aspect of QA Sphere is designed with security in mind. Our approach allows you to focus on delivering quality software while trusting that your data is safeguarded by advanced measures and a dedicated team committed to your peace of mind.

System Redundancy
Our cloud infrastructure ensures full redundancy and resilience, minimizing outages and achieving exceptional uptimes through robust system design and world-class data connectivity.

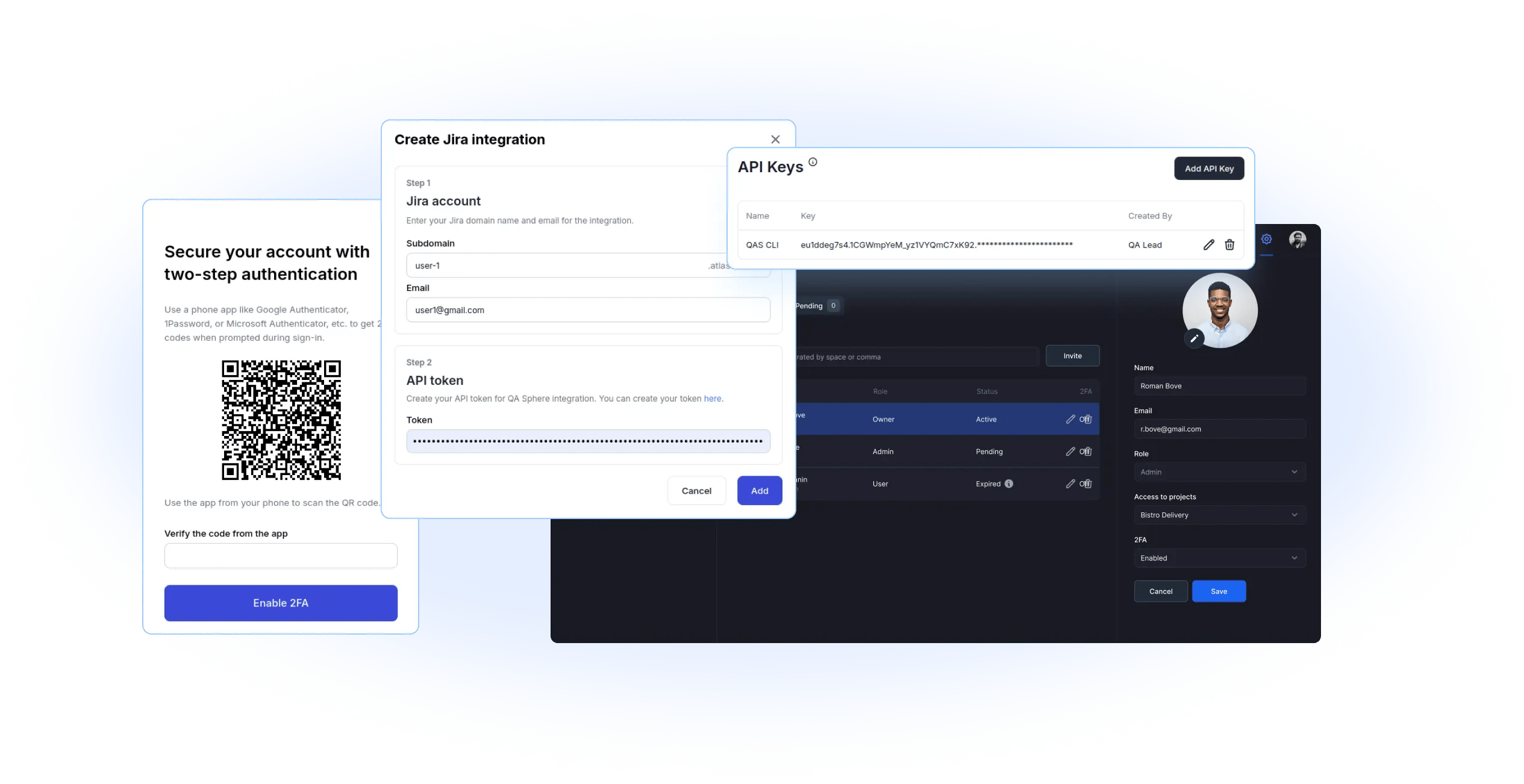
Access Permissions
RBAC ensures secure access management by assigning permissions based on user roles, restricting access to sensitive data, and enhancing system security and compliance.

24/7 Active Monitoring
Continuous monitoring detects and mitigates potential threats in real-time, ensuring system reliability, security, and uninterrupted performance around the clock.
AWS Infrastructure
Our platform is hosted on Amazon Web Services (AWS), leveraging its compliance with globally recognized standards such as ISO 27001 and SOC 2.
QA Sphere benefits from AWS data centers, which employ advanced physical security measures, including access controls, surveillance, and redundant power supplies.

HTTPS Encryption
All data exchanges are secured with HTTPS/TLS encryption, ensuring confidentiality and integrity to protect sensitive information from unauthorized access or interception.

Trusted Infrastructure
Built on Amazon AWS, QA Sphere leverages state-of-the-art data centers and systems to ensure reliability, scalability, and the highest standards of performance and security.

GDPR Compliance
QA Sphere adheres to GDPR regulations, ensuring the protection of personal data, transparent processing practices, and full compliance with privacy rights across all operations and integrations.

Audit Log
The audit log tracks all user actions, providing a detailed and transparent record of changes to ensure accountability, enhance security, and improve collaboration.

Sign In with Google
Sign In with Google works great for companies using Google Workspace, making login both simple and secure. SAML/OIDC-based SSO is coming in 2026!

Two-Step Authentication
QA Sphere enhances security with two-step authentication, requiring a password and verification code to prevent unauthorized access, even if your credentials are compromised.